Artificial intelligence is for us in every aspect of life, from phones and applications to search engines and even DrivingFor some reason. The fact that we are now getting web browsers with artificial intelligence assistants baked goods and chat chat shows that the way in which some people use the Internet to search for information and its consumption today are completely different from a few years.
But artificial intelligence tools require more and more total levels to reach your personal data under the guise of the need to work. This type of access is not normal, and it should not be normalized.
Not so long ago, you will be right to ask about the reason for trying to apply the free “Calculator” that appears to be not harmful, and even your data in actual time. These applications may not need these data to work, but they will ask them if they think they can make a Back or two by liquefying your data.
These days, artificial intelligence is not different.
Take the latest web browser in Perplexity, Comet, for example. The comet allows users to find answers using the integrated Amnesty International search engine and automate routine tasks, such as summarizing emails and orthodontic events.
In a rear training process with the browser, Techcrunch found that when the confusion requires access to the user’s Google’s Google Calendar, the browser requests a wide range of permissions to the user’s Google account, including the ability to manage drafts and send fully emails, download your contacts, display your events on all your calendar, and even the ability to take a copy of your company completely.
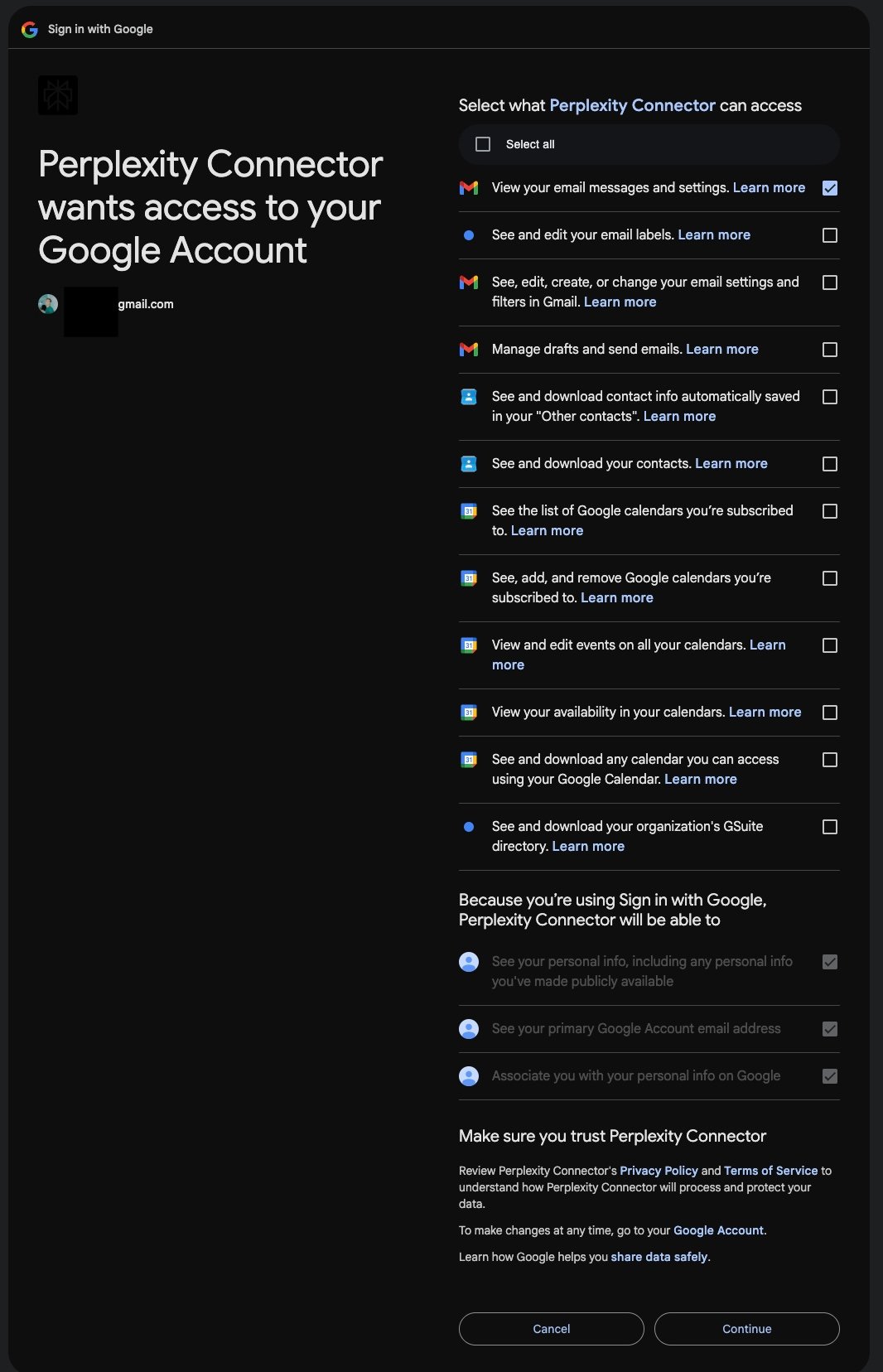
Al -Hirah says that many of these data are stored locally on your device, but you still grant the rights of the company Access and use Your personal information, including improving the artificial intelligence models for all.
Confusion is not alone to request access to your data. There is a trend for artificial intelligence applications that provide time to you by copying your calls or business meetings, for example, which requires Amnesty International to reach your own conversations in actual time, calendars, contacts, and more. Meta also tested the limits of what AI applications can access, including taking advantage of the images stored in the user camera roll that has not yet been downloaded.
The signal of the signal, Merridith Whitaker, recently enlarged the use of artificial intelligence agents and assistants, “putting your mind in a jar.” Wittker explained how some artificial intelligence products can prepare all kinds of worldly tasks, such as reserving a table in a restaurant or booking a ticket for a music party. But to do this, Amnesty International will say that it needs your permission to open your browser to download the website (which can allow AI to reach stored passwords, reference signals, your browsing record), and a credit card for reservation, and your calendar to determine the date, and you may also require opening your contacts so that you can share reservation with a friend.
There are serious risks of security and privacy associated with the use of artificial intelligence assistants who depend on your data. By allowing access, immediately and irreversibly based on handing over the rights of a complete snapshot to your personal information from that moment on your own incoming box, your letters, evaluation entries dating back to years, and more. All this in order to do a task that provides you with time – or, to the Whitaker point, saves you from having to think about it.
You also give the artificial intelligence agent to act independently on your behalf, which requires you to put a huge amount of confidence in a technique that is already vulnerable to the error of things or making things categorically. Using artificial intelligence also requires you to trust companies that seek to obtain profits that develop these AI products, which depend on your data to try to make artificial intelligence models better. When things do (and they do, a lot), it is a common practice for human beings in artificial intelligence companies to look at your own demands to find out why things do not work.
From the point of view of safety and privacy, the simple analysis of the costs and benefits is not worth delivering artificial intelligence to your largest personal data abandoning your information. Any AI application that requests these levels of alarm bells must be sent, just like the lamp application that wants to know your site at any moment of time.
Looking at the data processes you receive to artificial intelligence companies, ask yourself whether what you get is really worth it.









